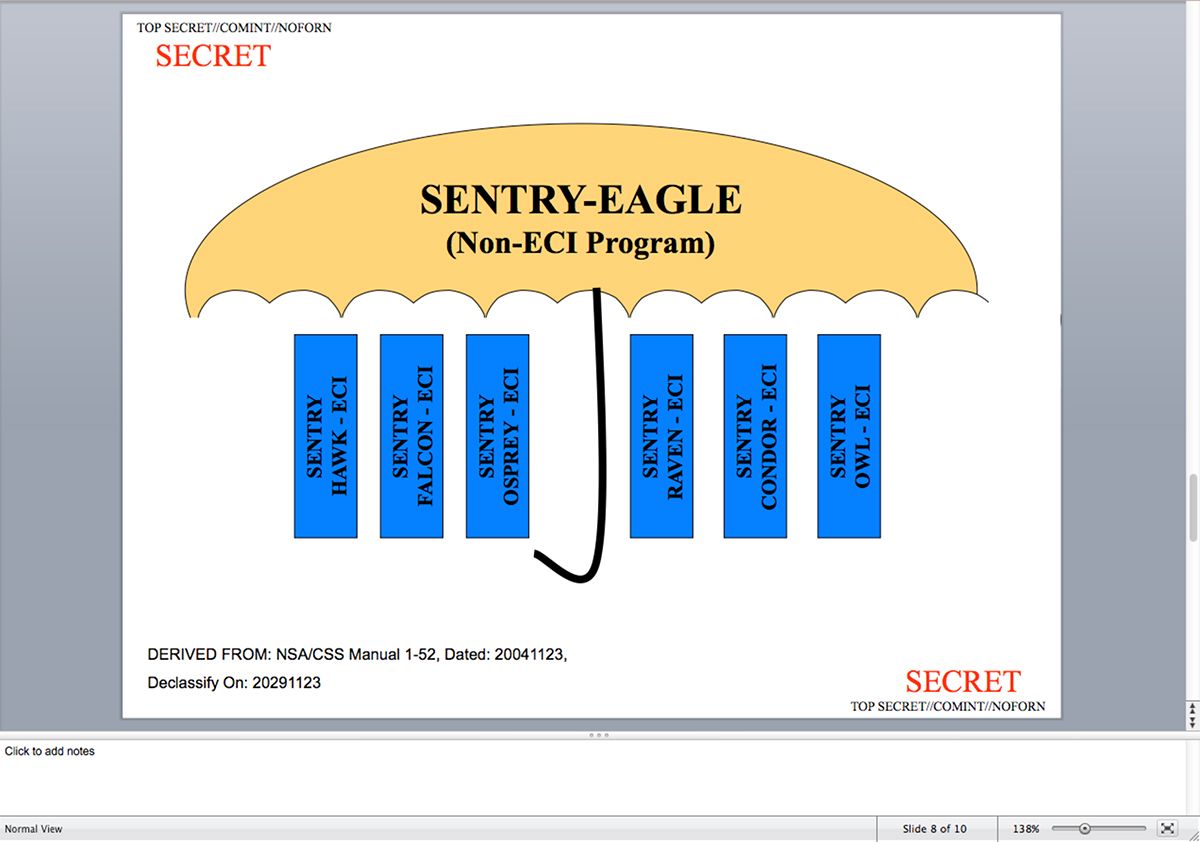
Snowden Movie Misses Key Purpose of NSA Spying – Monitoring CIA Covert Operations
The movie Snowden by Oliver Stone performs a masterful job in depicting efforts by the National Security Agency (NSA) in comprehensively gathering up electronic communications between people and organizations in the U.S. and all over the world. Stone correctly displays the routine violation of U.S....